Enhance Crypto Security: Level Up with Two-Factor Authentication
2024/03/11 17:17:05
In this article, we will explore how 2FA works, its importance in modern cybersecurity, and how it can be effectively implemented to protect your online presence.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a critical security measure that adds an extra layer of protection to your online accounts. Unlike traditional password-only approaches, 2FA requires users to provide two distinct forms of identification before granting access. This combination of something you know (like a password) and something you have (such as a smartphone app or a text message code) significantly reduces the risk of unauthorized access, making it a vital tool in safeguarding personal and professional data in our increasingly digital world.
How Does 2FA Work?
2FA operates by requiring two different types of evidence to verify a user's identity, thus creating a dual-layered defense against unauthorized access. The first factor is usually something the user knows, such as a password or a PIN. The second factor involves something the user possesses, like a mobile device that receives a unique code via SMS or an app generating time-sensitive codes. This process ensures that even if a password is compromised, unauthorized users are still blocked from accessing the account without the second verification step.
How Does 2FA Enhance Security and Why Do You Need It?
2FA has become increasingly crucial in the realm of online security. Traditional passwords, while widely used, have inherent vulnerabilities. They are susceptible to a variety of attacks, such as brute force, where attackers try numerous combinations until they breach an account. Moreover, the common practice of selecting weak or predictable passwords weakens their effectiveness. The frequent occurrence of data breaches and the subsequent circulation of compromised passwords across various online platforms have further eroded the reliability of password-only security.
2FA provides an added layer of security that significantly mitigates the risk of unauthorized access. While it is not entirely foolproof against cyber attacks, 2FA substantially increases the challenges faced by potential intruders, making it a vital component in safeguarding online accounts. By combining these distinct authentication methods, 2FA provides a robust security solution that significantly minimizes the risks associated with compromised credentials, thereby safeguarding sensitive data against emerging cyber threats.
Exploring Different Types of 2FA
This section delves into the various types of 2FA, each offering unique benefits and facing specific challenges. From the widely used SMS-based methods to the advanced biometric systems, we explore how each type fortifies security differently, addressing their accessibility, reliability, and potential vulnerabilities. Understanding these distinctions is key to choosing the most suitable 2FA method for personal or organizational needs.
・SMS-based 2FA:
This method sends a one-time code via text message to your phone. It's highly accessible and simple, but can be compromised through SIM swapping attacks and is dependent on cellular network reliability.
・Authenticator Apps 2FA:
Apps like Google Authenticator provide time-based One-Time Passwords (OTPs) offline. They offer offline access and can manage multiple accounts, but require initial setup and are dependent on having the device with the app.
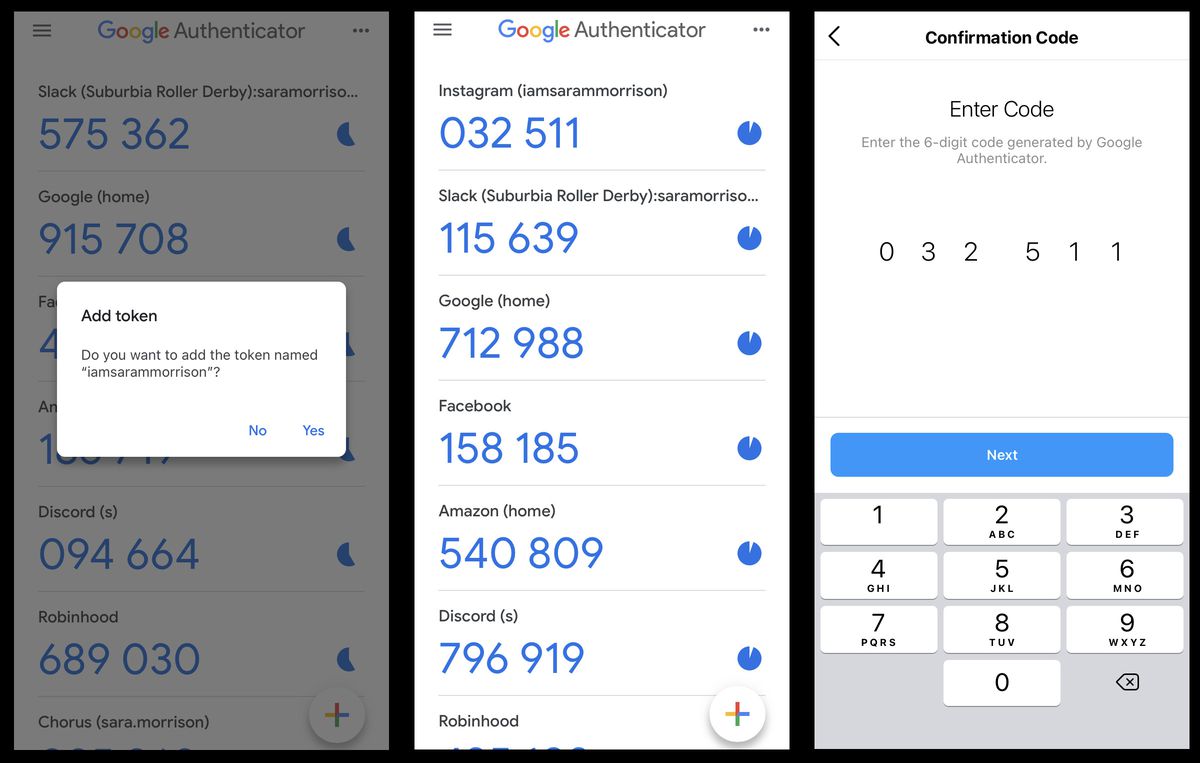
Google Authenticator, image from Vox
・Email-Based 2FA:
A one-time code is sent to your registered email. It's familiar and requires no extra devices, but is vulnerable to email hacking and may have delayed delivery.
・Hardware Tokens 2FA:
Devices like YubiKey generate OTPs and are highly secure, being immune to online attacks with long-lasting batteries. However, they incur an upfront cost and can be lost or damaged.
・Biometrics 2FA:
This type uses unique physical traits like fingerprints for identity verification. It's highly accurate and user-friendly, but raises privacy concerns and can sometimes produce errors.
Simple Guide to Securing Your Account With Two-Step Verification
Securing your account with two-step verification is a crucial step in protecting your online presence, but it involves more than just enabling the feature. Here’s a simple guide to ensure you’re getting the most out of this security measure:
Save Your QR Codes and Private Keys
When setting up two-factor authentication (2FA) using an authentication app, you are often presented with a QR code and a private key. These elements are crucial for regaining access to your account in situations like losing your phone or when setting up the authentication app on a new device. It's imperative to save these securely. A best practice is to print them out and store them in a secure location, such as a locked safe. Alternatively, you could store them in a secure, encrypted digital vault. Remember, losing these keys can make it extremely difficult to regain access to your accounts, so their security is as vital as the security of your passwords.
Private Keys Are Used for 2FA
Private keys play a critical role in the two-factor authentication process. They are essentially the 'secret' that's used to generate the codes you see in your 2FA app. Because these keys can create login codes for your accounts, they must be kept absolutely confidential. If a hacker gains access to your private key, they could potentially bypass your 2FA and gain unauthorized access to your accounts. Treat these keys with the same level of security as you would your most sensitive passwords.
Keep Backup Codes, QR Codes, and Private Keys Offline and Safe
To safeguard your accounts, it's crucial to keep backup codes, QR codes, and private keys offline. Storing this information online or on a connected device can leave it vulnerable to cyber-attacks. Physical storage, such as writing them down and keeping them in a secure, fireproof safe, is recommended. Alternatively, you could use an offline digital storage device, such as a USB drive that you store in a secure location. This ensures that even if your online security is compromised, your backup methods remain safe and inaccessible to potential hackers.
Beware of Phone-Based Attacks
While 2FA adds a layer of security, it's important to be aware of phone-based attacks like SIM swapping. In such attacks, a hacker tricks your mobile provider into transferring your phone number to a new SIM card. This gives the hacker access to any SMS-based 2FA codes sent to your number. To protect against this, consider using an authenticator app that generates codes without needing a text message. Additionally, keep an eye on your phone's network connectivity; an unexpected loss of service could indicate a SIM swap attempt.
Use Strong Passwords and Unique Email Addresses
A strong foundation for account security starts with using robust, unique passwords for each of your accounts. Avoid common phrases, predictable patterns, and personal information in your passwords. A combination of letters, numbers, and special characters can significantly enhance password strength. Additionally, using different email addresses for various types of accounts (like personal, work, and financial) can help contain the damage if one of your email addresses is compromised. This practice helps ensure that a breach in one area does not lead to a domino effect, compromising other areas of your digital life.
No Security Solution Is Foolproof
It's vital to recognize that no security system is entirely impenetrable. Cyber threats are constantly evolving, and what works today might not be sufficient tomorrow. Therefore, staying informed about the latest security threats and best practices is crucial. Regularly review and update your security settings, and be proactive in checking for signs of unauthorized access. If you notice anything unusual, such as unfamiliar login attempts or changes in account settings, take immediate action. This could include changing your passwords, reviewing your account recovery information, or contacting the service provider for assistance.
By incorporating these expanded key points into your strategy, you can significantly enhance the security of your accounts with two-step verification. This not only makes it much harder for unauthorized individuals to access your sensitive information but also gives you greater peace of mind in the digital world.
How to Enable 2FA for FameEX?
Selecting a two-factor authentication (2FA) method should be based on considerations like security needs, ease of use for the user, and the context in which it is being used. For scenarios demanding heightened security, such as managing financial or cryptocurrency exchange accounts, the use of hardware tokens or authenticator applications is often recommended. On FameEX, we support eight different types of security setups to help safeguard your account including two-factor authentication (2FA). Here is a quick demonstration of how to enable them.
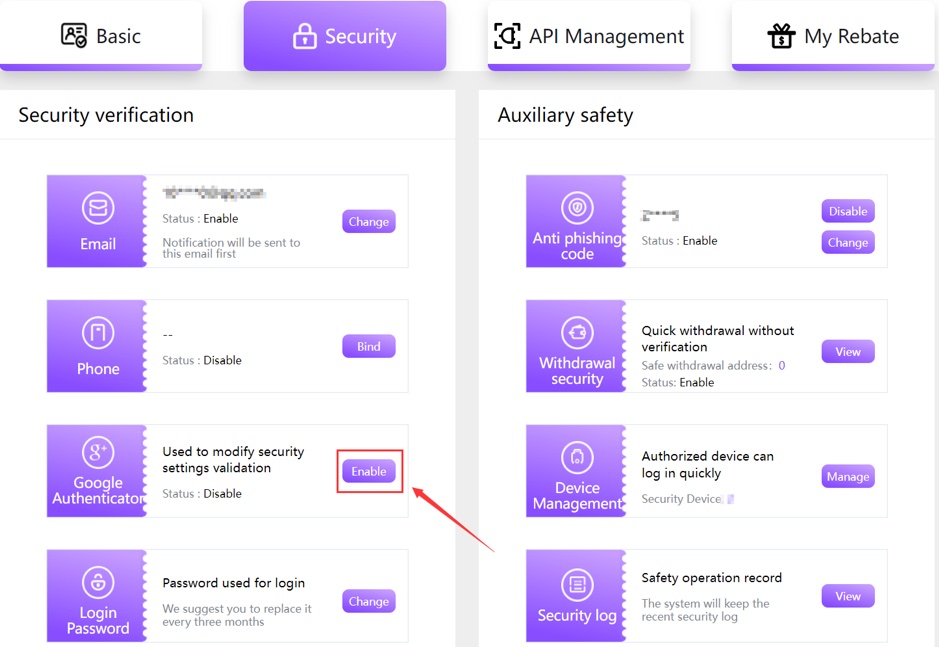
To enable your Google 2FA on FameEX, first log into your account and navigate to the [User Center] icon, then select [Security]. Under the [Security] tab, find [Google Authenticator] and click [Enable]. Next, click [Send] to receive a verification code in your registered email, which you need to enter promptly before clicking [Next]. Download and install the Google Authenticator app on your mobile device, and use it to either scan the QR code or manually input the provided key for verification. Finally, enter the 6-digit code from the app and click [Confirm] to successfully add your Google 2FA. For more information on how to set up your FameEX 2FA feature, please refer to the guide in our support center.
Conclusion
Utilizing Two-Factor Authentication (2FA) is essential, not just an option, for enhancing online security. It's a critical step in safeguarding accounts, especially those related to finances and investments, including cryptocurrency. To effectively use 2FA, it's important to regularly update your authenticator app, enable 2FA on all eligible accounts, and continue using strong, unique passwords. Stay vigilant against sharing OTPs, falling for phishing scams, and verify the authenticity of requests. Remember, online safety is an ongoing process; staying informed and alert to new technologies and threats is key to maintaining your digital security.
FAQ Crypto Authenticator
Q: How Do I Set Up 2FA?
A: To set up Two-Factor Authentication (2FA), first, choose a 2FA method (like an authenticator app or SMS). In your account settings, typically under 'Security', find the option to enable 2FA. Follow the instructions, which usually involve scanning a QR code with your authenticator app or entering a phone number for SMS. Finally, confirm the setup by entering the code provided by your chosen 2FA method.
Q: How to Reset My 2FA?
A: To reset your 2FA, log into your account and navigate to the security settings. Look for an option like 'Reset Two-Factor Authentication'. You might need to verify your identity through alternative methods provided by the service, such as answering security questions or using backup codes. After verification, you can set up a new 2FA method following the usual setup process.
Q: Why 2FA Is Important in Cryptocurrency?
A: Two-Factor Authentication is crucial in cryptocurrency due to the irreversible nature of crypto transactions. Once a transaction is made, it can't be undone. This makes crypto accounts prime targets for hackers. 2FA adds an extra security layer, making it much harder for unauthorized users to gain access to your crypto wallets and funds.
Q: How to Keep Your Accounts More Secure?
A: To keep your accounts more secure, use strong, unique passwords for each account and enable 2FA. Regularly update your software and apps to the latest versions. Be vigilant against phishing attacks by verifying the sources of emails and messages. Additionally, monitor your accounts for any unusual activities and use secure networks, especially when handling sensitive information.
Q: What Is a Mnemonic, or Secret Code, Seed, or Recovery Phrase?
A: A Mnemonic, also known as a Secret Code, Seed, or Recovery Phrase, is a series of words generated by your cryptocurrency wallet. It acts as a master key to recover your wallet's private keys and funds if your device is lost or damaged. It's crucial to keep this phrase extremely secure and private, as anyone with access to it can control your crypto assets. It should be stored offline in a secure location.
The information on this website is for general information only. It should not be taken as constituting professional advice from FameEX.
